Wireless Security Sins
Securing a Wireless Network is a continuous process, an ongoing war of escalating threats and solutions. As new 802.11 standards roll out, additional tools in your arsenal become available to utilize.
Beyond updating your network with newer hardware in order to support the advanced security standards, client devices also need to continuously updated as a complete system.
Finally, the security settings are useless if they are not enabled and enforced. This article will review some common mistakes done in the implementation of security standards.
Do Not Use a PSK if the Clients can support 802.1x
If you can avoid having a Pre-Shared Key (PSK) authentication method on any of your WLANs, it is always best to do so. This security type is also called "personal” on some platforms, and as the name suggested is not intended for the enterprise environment.
Although PSK authentication is easy to set up, this is what most people use at home; and it may even be seemingly easy to manage without an additional Radius server, certificates, or individual accounts. Managing this type of WLAN can quickly become quite difficult if you wish to keep it even slightly secure.
Having a single password (PSK) that is shared among all clients makes it very easy to lose track of who exactly has that password and which clients are legitimate users. Once the password is out in the open, anyone who knows the password has access to the network and also can decrypt that data clients are sending if they are not using additional security like a VPN. It is also easy to create a fake Access Point to capture users with a man-in-the-middle attacks.
If the pre-shared key password is weak, it can be easily cracked with a dictionary attack. Weak passwords are actually very common, since the longer and more difficult the password, the harder it is to remember and the harder it is to enter a long-complicated password into all of the devices. Complex passwords lead to employees writing it down on sticky notes and whiteboards, pictures taken of the password and shared when devices need to be added.
The larger the client base, the more difficult it is to keep that password contained, and in the event the password is compromised, all of the clients will need to be manually reconfigured with the new password. Rotating the password on a regular basis can help with removing clients that should no longer have access, but it is only as effective as the frequency of the rotation, and with every client needing to enter in the new password it encourages spreading the password less securely
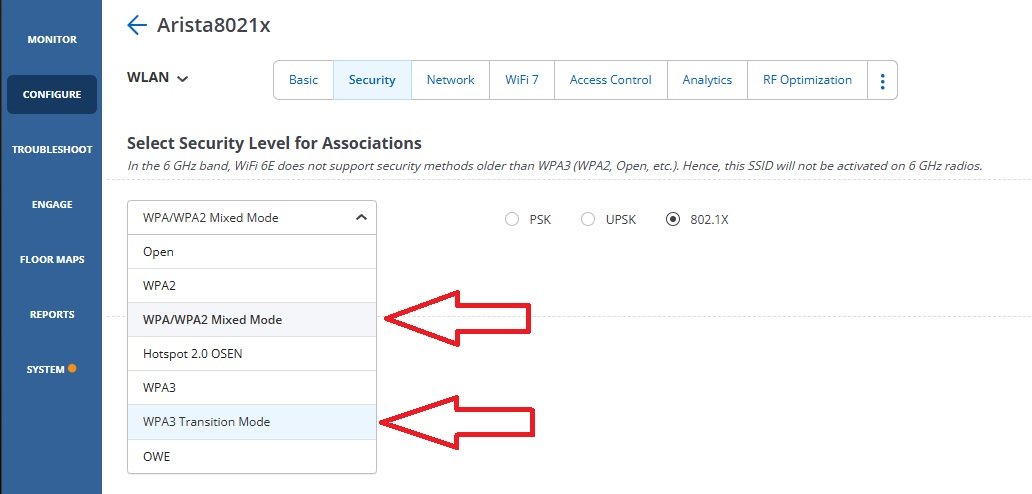
Do Not Allow Security Based Mixed Modes or Transition Modes
When setting up a WLAN with 802.1x, often there is an option of enabling a “mixed mode” or “transition mode”. The premise is to allow older clients to authenticate to the network with older less secure authentication and encryption method. Mixed mode is usually allowing the client an option of WPA with TKIP instead of WPA2 with AES. In the WPA3 Transition, WPA2 is utilized instead of WPA3 and other security features such as 802.11w PMF are also not required.
The network is only as strong as the weakest settings and having clients use those weaker settings, it invites attacks on those clients and potential access to that client’s data and/or access to your network.
It also gives the false impression for users and management that there are higher security settings in use and no further action is required in the future.
A much better solution is to segregate clients that cannot support the advanced security settings onto a separate WLAN and VLAN that can be contained with additional backend considerations such as additional firewall rules. When all legacy clients have been upgraded this less secure WLAN can be removed.
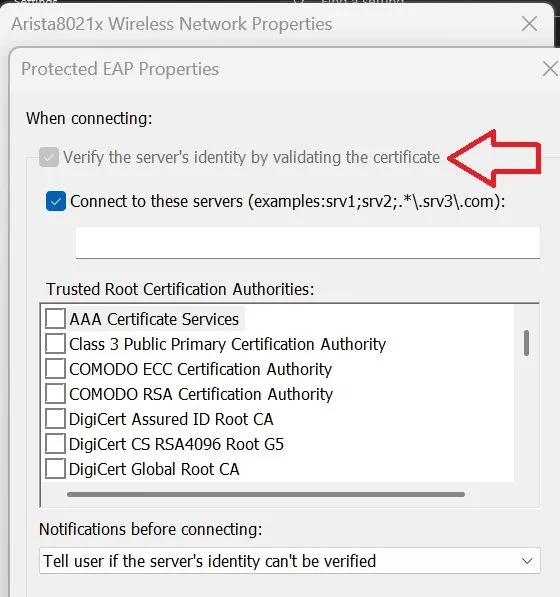
Do Not Disable Certificate Verification on your Clients when using PEAP
One of the best features of PEAP is the ability to verify the network you are connecting to is not a fake honey-pot network by verifying the certificate presented during authentication.
It is also this certificate that is utilized for the TLS Tunnel encryption, so if you are letting the client device connect without verifying the certificate, anyone can fake the WLAN and certificate and translate the encryption of the data on the WLAN.
Make sure to have your clients not bypass this step to ensure their data is secure.
Do Not have Multiple WLANs with different Security Settings for the same VLAN
For the same reasons you should not have multiple security methods on the same WLAN, if multiple WLANs connect with different security methods to the same VLAN you might as well only have the weaker WLAN in usage. Always segregate different WLANs with different levels of security into their own unique VLANs. In that way you can eliminate these weaker WLANs and VLANs in the future and add additional Firewall rules for the weaker security zones.
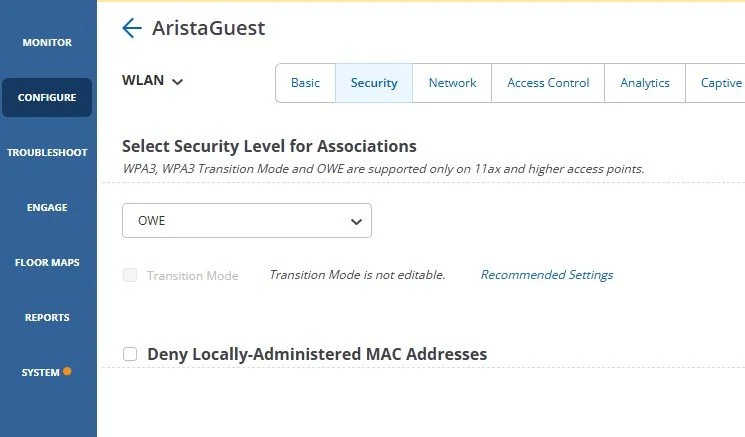
Do Not have OWE Turned Off on your Open Networks
If your WLAN is not already utilizing encryption, such as for a Guest network, turning on Opportunistic Wireless Encryption (OWE) should be enabled to protect the client data. It will not help with authentication, only encryption. This solution is best suited for Guest networks that utilize splash pages.
Do Not have 802.11w Management Frame Protection Disabled
Protecting the management frames with 802.11w is significant enough that it has become a requirement of 6GHz and Wi-Fi6e and beyond.
Attacking management frames is often a first step that is taken to force client re-authentication in order to capture the event where the client is most vulnerable. This is a component of spoofing and replay attacks.
Setting to PMF to required is always the best, but optional/capable is still better than having it completely disabled for WPA2 wlans.
Conclusion:
One of the largest factors of being able to enable more enhanced security is the function of your wireless clients being able to handle the newer protocols.
As judicious you need to be in enabling security settings on your network, equally you need to be active in making sure they clients are not falling so far behind that they cannot make use of these security settings and features.
There will always be a struggle between making a WLAN that is easy for your clients to access and one that keeps you clients and network secure.
Always remember, your network is only as secure as your least secure client.