Guest Wireless Network DOs and DON’Ts
In today’s business world, having a Wi-Fi network available to you has become a professional requirement. This expectation of Wi-Fi access carries over to when visiting other companies where guests will need to stay connected to their email, continue to attend virtual meetings, and access their business sites and applications.
When setting up your Guest network there are a few Do’s and Don’ts you should follow to help not only protect your network but also your Guests as they are connected. We will explore these settings in the article below utilizing Arista’s Cloud Vision Wireless Manager as the configuration examples.
Most of these recommendations are focused on a business that has visitors hosted during business hours. Hotels and hospitality businesses, where Guests users will be accessing personal resources, should have different expectations and requirements that may differ from what is suggested in some circumstances.
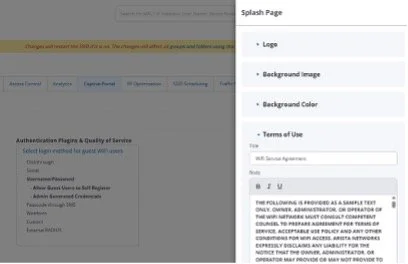
DO: Use a Splash Page with a “Term of Use”
It is always the hope that your Guest Clients will use your network as intended, and nothing nefarious, but it is highly advised to lay out the Terms of Use that clearly specify what your Guest Network cannot be used for.
In the event there is an incident, those that were misbehaving cannot claim that they were unaware that they were in violation of your policies.
If the Guest Network is already using a Captive Portal, it is simplistic to add the Terms of Use to the Splash Page:
DO: Use an Application Firewall
If your network has it, an Application Firewall is a great tool to prevent unwanted traffic or usage if the Guest user decides that they do not want to follow the Terms of Use.
Everything from adult content websites, gaming, social networking, to file transfer sites can all be blocked. Anything that is not appropriate for running over the company network or even sites that consume a lot of bandwidth by streaming videos or uploading files can be prevented. This can stop many issues and events before they are allowed to occur.
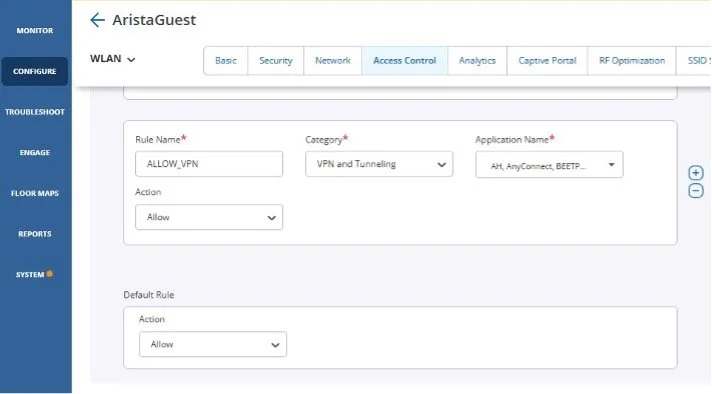
DON’T: Block VPN for your clients
While being a guest at your facility, it is reasonable to assume that Guest Clients will need to connect back to their business resources. This service should be the main reason for hosting a Guest Network.
VPN is also an excellent way for the clients to protect themselves and their data while using your guest network, especially if the Guest wireless network does not currently utilize OWE.
You can create a rule to allow, or just make sure not to block if the default rule is Allow:
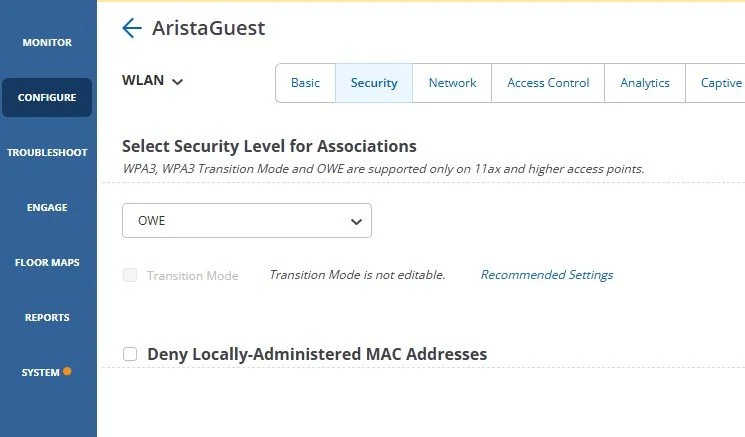
DO: Enable Opportunistic Wireless Encryption
Opportunistic Wireless Encryption (OWE) is a great way of helping keep your clients’ data private, especially in a Guest network where user authentication is not present.
There are limitations for this feature, your Access Points will need to be new enough to support the feature. Also, your Guest clients will need to be able to support it.
Even with these limitations, encrypting the data on what would otherwise be an open network can give users privacy regardless of whether they are employing a VPN.
Do not confuse the encryption for proper authentication, it is not a replacement for WPA2 or WPA3, and does not help with authentication:
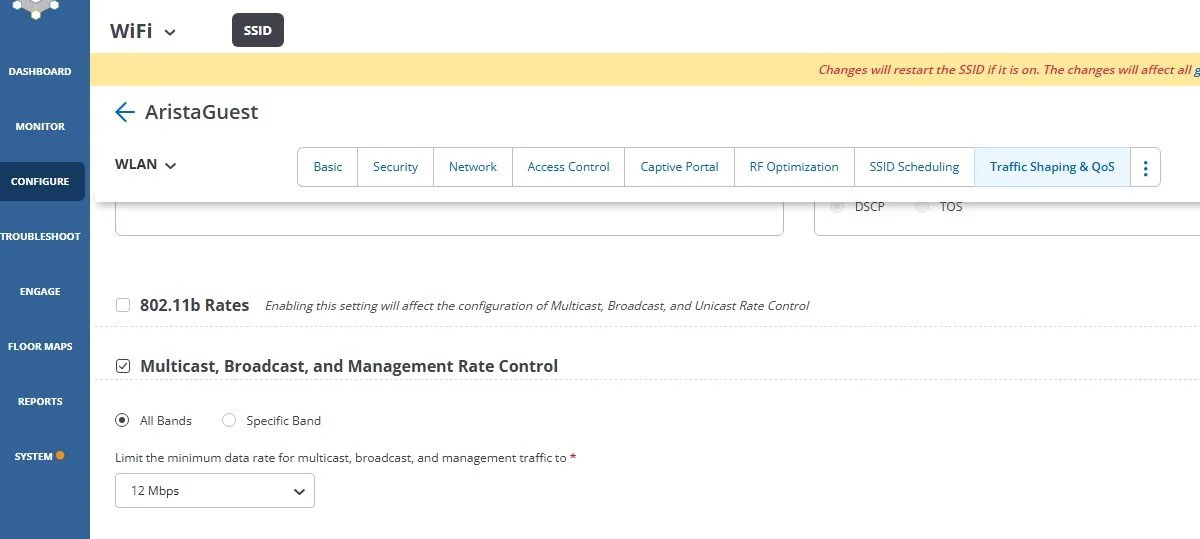
DON’T: Leave Lower Data Rates Enabled
Wanting to be more compatible with older clients, it might be tempting to keep older data rates and protocols enabled.
However, doing so can negatively impact the rest of your wireless network. Clients that join with older modulation rates will slow down any other wireless clients on the same channel potentially impacting your production wireless networks even though they are on a different SSID.
Clients on lower modulation rates can become “sticky” and resist roaming to more optimal Access Points, slowing down the spectrum further.
Slower modulation rates can also travel farther, meaning that you could have people successfully access the Guest network well outside the walls of your facility. This could include people who wish to misuse your wireless network and can do so not even on the company property.
DON’T: Configure Long DHCP Lease Times
Clients on a Guest network are extremely dynamic, and like any good guest, should be departing after a short stay. The lease times for Guest should reflect that.
SSIDs that utilize a captive portal will give out a DHCP lease before any type of authentication is passed, meaning that you will start losing DHCP addresses to clients that cannot even successfully authenticate to your Guest Wireless Network.
Depending on the size of your DHCP scope, you can quickly run out of addresses while waiting for the leases to expire, preventing new clients from successfully connecting.
Setting your DHCP time out values to expire within a couple of hours should ensure only active wireless users are taking up those valuable IP addresses.
DO: Isolate your Guest VLAN
Your Guest Wireless Traffic should be on a separate VLAN from your production network to help with isolating the traffic from the production network. This VLAN should route only out to the Internet if possible and have a proper Firewall in place to limit where devices in the subnet can reach. If your wireless network utilizes a cloud wireless controller or it is an autonomous system, this will require trunking the Guest VLAN to each Access Point, if utilizing a local Wireless Controller and not implementing a Flex solution, you only need to trunk the Guest VLAN to the Controller itself.
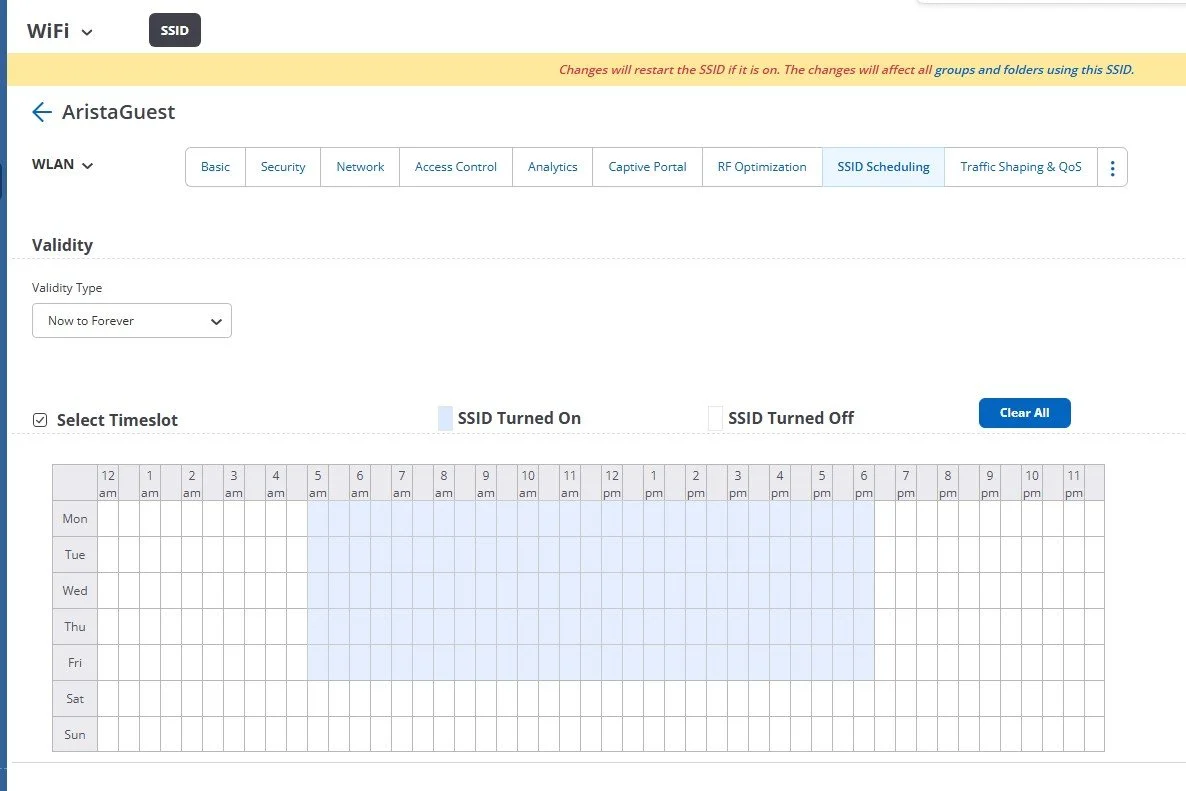
DON’T: Have your Guest SSID running after Business Hours
It is recommended to restrict the time that your Guest Network is in operation to when you should reasonably have Guests on your network.
If the office closes at 5:00pm, then there is no reason that you would have a Guest client connected and running long after that time. Perhaps leave the Guest network on for an additional hour or so, for meetings that are running late, but allowing the network to be accessible at 3:00am is not in your best interest.
Having your Guest Wireless Network available after business hours entices its usage for reasons not intended or desired. It also allows access when your employees are no longer present to monitor the Guest Users and their activity.
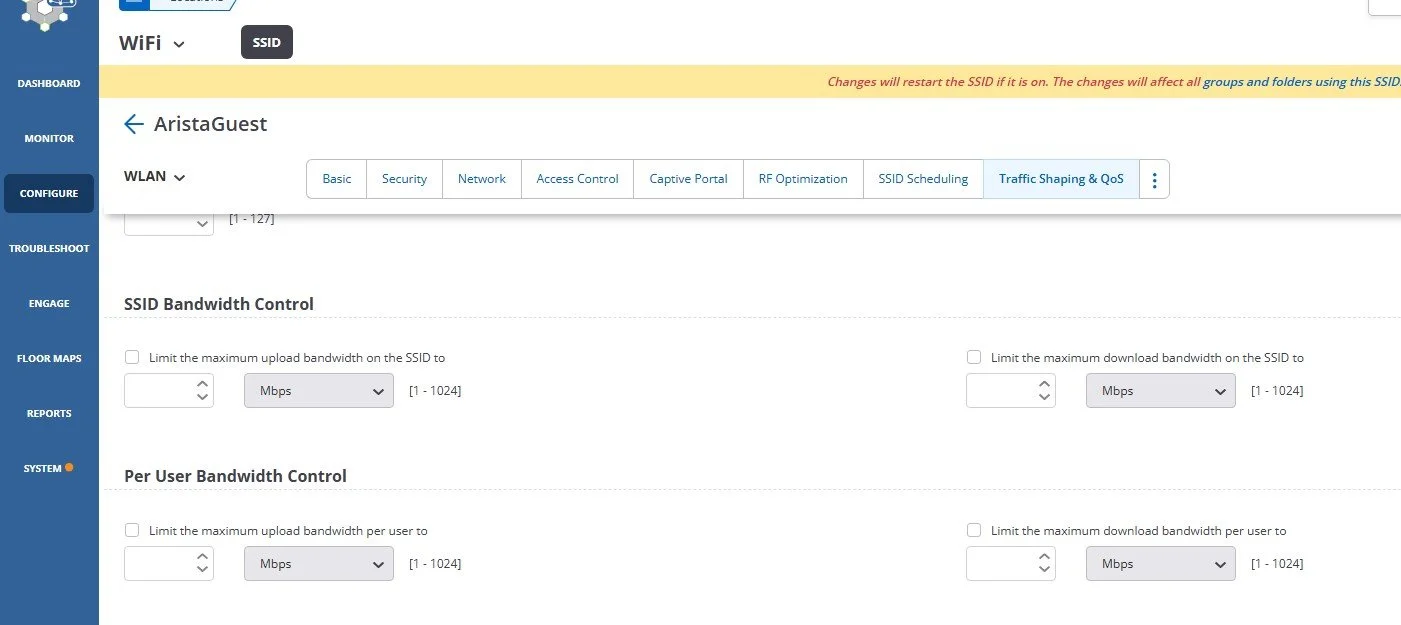
DO: Limit Bandwidth on the Guest SSID or Per Guest User
The number of Guest Users can fluctuate greatly, as well as the amount of bandwidth they will consume. The amount of bandwidth on your uplinks to the Internet will be consistent. A calculation on how much bandwidth the Guest network should consume is a value that needs to be calculated both upstream and downstream; and should be set accordingly. For further refinement, and to be fairer for all the Guest Users, per user settings can be implemented so that no single user monopolizes the bandwidth of the Guest Wireless Network:
DO: Lower QoS Priority
Before the Guest Traffic hits the Internet, it will still need to pass through the production network. To ensure that traffic from the Guest Wireless Network has a lower priority than your production network, enabling QoS is advised.
Start by setting the Guest Wireless Network to “Best Effort” and further refining from there:
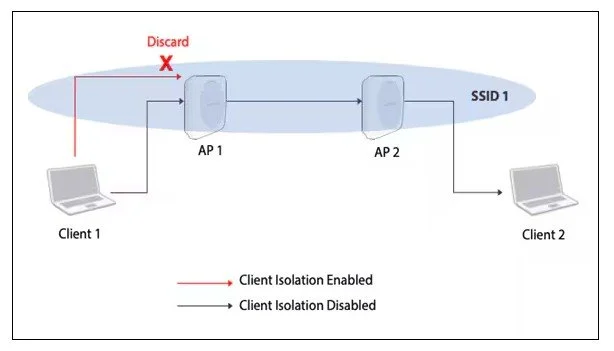
DO: Activate Client Isolation
Before the Guest Traffic hits the Internet, it will still need to pass through the production network. To ensure that traffic from the Guest Wireless Network has a lower priority than your production network, enabling QoS is advised.
Start by setting the Guest Wireless Network to “Best Effort” and further refining from there:
DON’T: Hide your SSID
Hiding your SSID does not make it more secure, and it makes it a lot more difficult for your Guest Clients to find and connect.
It will force your Guests to enter in the SSID name exactly to join which can be extremely time-consuming and frustrating if the name has any complexity. This will also add an extra layer of troubleshooting if clients cannot join the network. It also makes it easier for a nefarious user to broadcast a fake Guest network.
Conclusion:
Guest Wireless Networks are important to support clients, customers, and any other various visitors to your facilities; but allowing people to access your network comes with risks.
These risks, if not mitigated, can negatively impact the performance of your wireless production networks and/or put the data of your visitors or company at stake. There is a balance between making a Guest Wireless Network easy to access and making a Guest Wireless Network safe and secure for the company and visitors. Ultimately, where you and your company find that balance is up to you, hopefully these suggestions can help you along that path.